Enter your email address to receive the latest ITVET news, market insights, and useful IT tips.
In the ever-changing world of cyber security, businesses are always finding new ways to fend off threats. But there’s still one weak spot: people. Cybercriminals know this all too well, and they’re taking advantage of it. According to Verizon’s 2023 Data Breach Investigations Report, a staggering 74% of breaches happen because of human errors or manipulation. And those sneaky social engineering attacks? They’re on the rise and getting trickier by the day. So, it’s high time businesses get clued up on how to prevent social engineering in the workplace.
What is social engineering in cyber security?
Social engineering in cyber security is a broad range of malicious activities that exploit human behaviours and natural tendencies. Using psychological manipulation, cybercriminals gain the trust of their targets, so they lower their guard. This makes it easier for them to trick their targets into taking unsafe actions such as divulging confidential information, clicking on fake web links, or downloading malicious attachments.
Businesses saw a spike in social engineering attacks during the COVID-19 pandemic. Remote working and heightened emotions made them more vulnerable and at risk. Cybercriminals heavily exploited the situation and would often launch their attacks after a government announcement to increase their chances of success.
How does social engineering work?
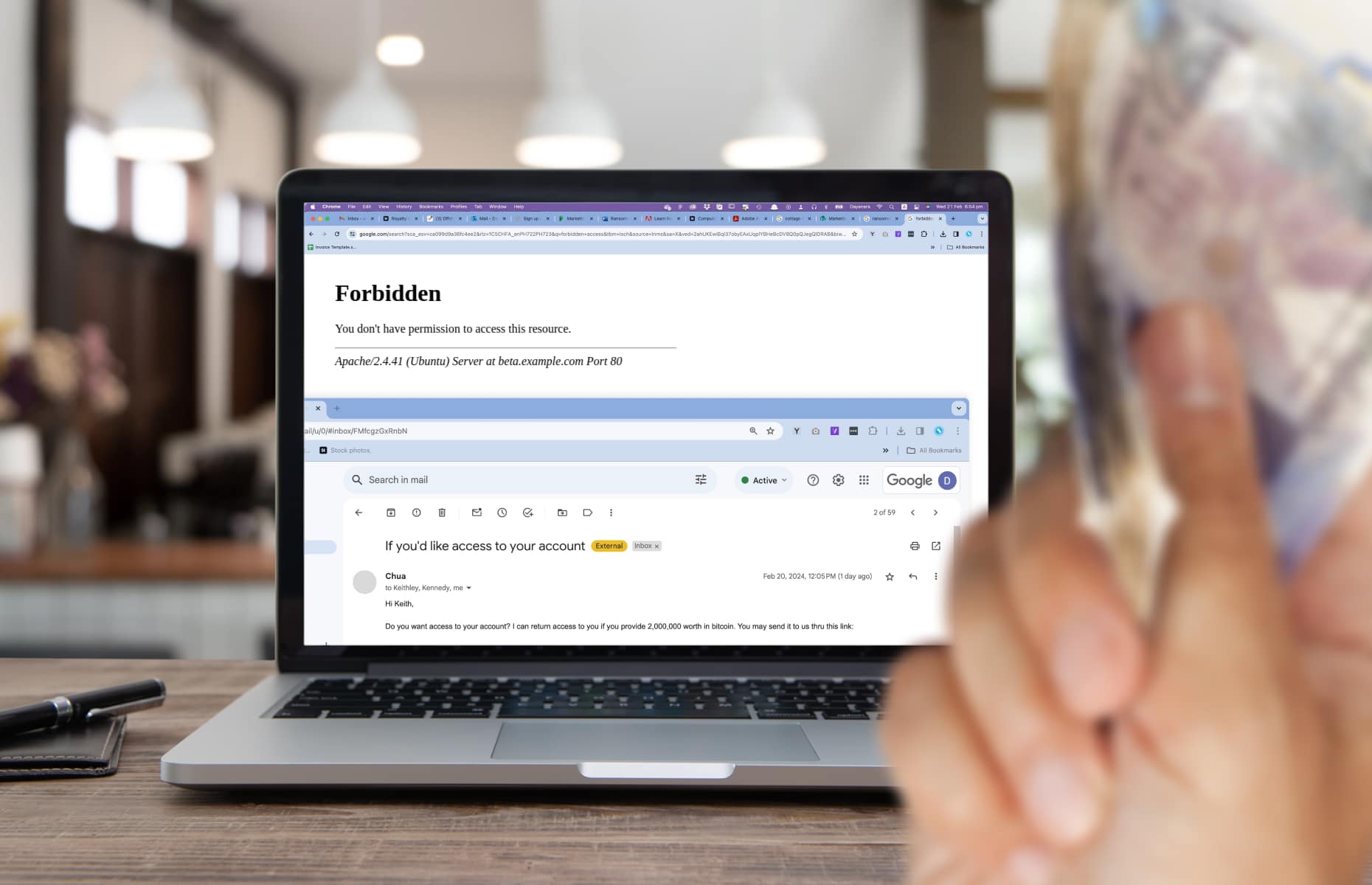
In a typical digital social engineering attack, a cybercriminal impersonates a trusted organisation to lull their target into a false sense of security. They’ll make contact with the unsuspecting victim, usually via email, and encourage them to take further action.
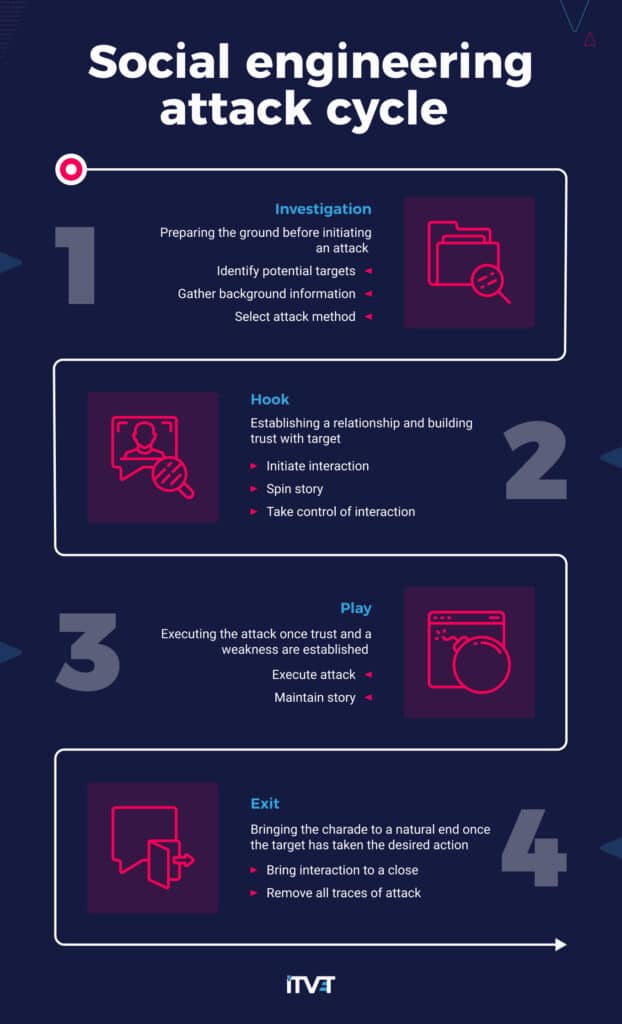
A social engineering attack cycle can be broken down into four key stages. This includes gathering information on the target, building a relationship with them, executing the attack, and bringing it to a natural end without arousing suspicion.
The diagram below highlights the four stages of a social engineering cycle:
What are the key dangers of social engineering?
- It doesn’t have to work against everyone. It only takes a single error of judgment for a cybercriminal to gain access to your network. And there’s not a single person alive who never makes mistakes.
- It relies on human error, rather than network or software vulnerabilities. Technology is predictable, and vulnerabilities can easily be identified and patched. People, on the other hand, are complex and unpredictable. You never know when they’ll make a mistake next, what mistake they’ll make, or if they’ll make it more than once, and if they do, will they report it? This is why people are the weakest link in cyber security.
- Social engineering attacks are becoming increasingly complex and more difficult to spot. For instance, Artificial Intelligence (AI) has opened the doors for cybercriminals. Anyone can use AI, regardless of the language they speak, to create convincing phishing emails and fake websites. AI-generated phishing scams look more realistic than ever and are less prone to the usual red flags, such as poor spelling and grammar.
What are the different types of social engineering attacks?
There are many different types of social engineering attacks, and they can happen anywhere human interaction is involved.
Here are the four most common types of social engineering attacks:
1. Phishing
Phishing is the most prevalent form of digital social engineering attack, accounting for 84% of cyberattacks on businesses. It uses email to trick victims into clicking a malicious link, downloading an infected attachment, or revealing private information.
Cybercriminals are becoming really good at masquerading as trustworthy sources such as retailers, clients, couriers, or government agencies. Phishing emails are also cleverly designed to create a sense of urgency, curiosity, or fear to make the victim act rashly without checking the email’s authenticity.
2. Spear phishing
Spear phishing is more targeted than a standard ‘blanket’ phishing attack. It focuses on one specific group or person within an organisation, such as the company’s systems administrator.
With this type of phishing, cybercriminals invest time and effort into learning personal information about their target. This might include details such as their job title and the contacts they regularly correspond with. This information is then used to create a highly personalised email from a legitimate source, making it much more likely to succeed.
3. Baiting
Baiting is a type of digital social engineering attack where the cybercriminal offers a valuable freebie to pique the victim’s greed or curiosity. For example, the victim might see an online promotion or receive an email that promises a free gift card if they take a survey. But, when they click on the link they’re redirected to a fake website where they’re lured into providing personal information.
4. Scareware
Scareware is a type of malware attack that uses social engineering to scare victims into making impulsive decisions.
One of the most common tactics is the fake virus scam. This uses pop-up messages to warn victims that their devices are infected and that they must take immediate action. The victims are then prompted to buy fake anti-virus software to ‘fix’ the issue before it’s too late. However, rather than fixing the issue, they usually lose their money and the software download installs malware on the computer system.

10 ways to prevent social engineering attacks
The good news is that there are proactive ways to prevent social engineering attacks. These differ in levels of complexity, from general maintenance and simple checks to more sophisticated protection that may require specialist support from an IT company like ITVET.
Here are our top 10 approaches on how to prevent social engineering:
1. Cyber security awareness training
Cyber security awareness training can help you avoid social engineering in the workplace. Ensuring your employees know the common red flags to look out for can help them identify social engineering attempts such as phishing.
2. Phishing simulations
Phishing simulations take awareness training a step further. As well as educating employees on cyber security, you can test their understanding with real-life simulations. This shows you how successful an actual phishing campaign would be and alerts you to any areas that need to be improved.
3. Email security
Email is one of the main ways to launch a social engineering attack, so it’s important that businesses have robust email security. This should include an effective spam filtering system that detects and quarantines suspicious emails before they reach the inbox.
4. Least privilege
Social engineering often relies on escalating privileges to gain access to an organisation’s network and systems. Zero-trust access ensures that users only have access to the resources they need. This minimises the risk and potential impact of a digital social engineering attack.
5. Password management
Effective password management is an important layer of defence against social engineering attacks. Make sure your business has a clear password policy outlining requirements such as minimum length and combinations, expiration dates and storage. Ideally, your business should also use a secure password manager such as Dashlane to protect and manage passwords.
6. Multi-factor authentication
Multi-factor authentication (MFA) gives your login credentials an extra layer of security. This means you need to provide extra information, such as a security question, one-time verification code, or a fingerprint scan.
7. Social media policy
Cybercriminals tend to collect intelligence on their targets via social media profiles. The more information they can gather, the more chances they have of success. Oversharing is a real issue and a key enabler for social engineering attempts such as spear phishing. Having a clear social media policy on privacy and usage can help prevent potential attacks.
8. Network monitoring
Around-the-clock vigilance can help enhance the security of your network and critical systems. Your network and systems should be monitored 24/7 to ensure vulnerabilities and threats are quickly identified and thwarted. This can be done remotely, so your network security can be outsourced to a managed service provider like ITVET to take the pressure off your in-house IT team.
9. Penetration testing
Penetration testing is one of the most effective ways to prevent social engineering attacks. Pentests allow you to identify vulnerabilities and flaws in your network and systems so you can patch them before they’re exploited by cybercriminals. We recommend you carry out regular penetration testing as part of a robust cyber security strategy. For the best results, the pen testing should be carried out by a third party who doesn’t know your systems, because they can expose blind spots missed by your internal IT team.
10. Security patches
Keep on top of your security patches and ensure your web browsers and systems are kept up to date with the latest versions. Maintaining your IT setup helps create a cyber-resilient environment to minimise the risk of a digital social engineering attack.

Final thoughts
The ‘human’ element is often ignored, yet it’s a critical element in building a strong defence against cyberattacks. Understanding how to prevent social engineering in the workplace is key to reducing the risk of being successfully targeted. Our team at ITVET can enhance your existing IT security with human-centric approaches to protect your business against social engineering attacks. Get in touch for a free consultation with one of our cyber security experts.